In the STEM world, technology is the fastest growing field. As the demand for high technology in our phones, computers, and televisions increases, so does the rate at which technology changes. Despite all these changes in tech, the fundamental principles remain the same. Technology relies on logic, encryption and decryption, and programming. These three unplugged science activities explore the fundamentals of computer programming without ever touching a computer!
Scytale Cipher
A scytale (meaning “cylinder”) is a tool to decrypt a hidden message. Historically, this was used by the Greeks and Spartans during military times and consisted of a piece of parchment with a message wrapped around a cylinder.
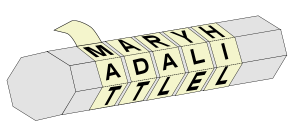
You can create your own scytale using any cylindrical object (soda can, water bottle, candle, hairspray bottle, etc.), masking tape or paper strips, and a pen. Wrap the masking tape around the object starting from one side and ending at the other. Using a pen or marker, write a message on the tape. Fill in any blank spaces on the tape with other letters. Remove the tape from the object. You’ll notice that your message has disappeared!

Try wrapping the tape around another cylindrical object. You won’t be able to read it because this object is a different diameter. The message you write original is decrypted (plaintext). When you add other letters and remove the tape from the object, the message becomes encrypted (ciphertext). The key to reveal and decrypt your message is to use an object with the same diameter. Pretty cool!
You can watch a full video of this activity on STEM Universe here.
Binary Bracelets
Binary is a base-2 numeric system only using 0s and 1s. It’s the way that data is stored in computers and all words, letters, and symbols can be translated into binary. A bit (or binary digit) contains a single binary number, a 0 or a 1. A byte is 8 binary digits. Large file sizes can contain many bytes. For example, a megabyte contains one million bytes!
All the letters of the alphabet have a binary equivalent:
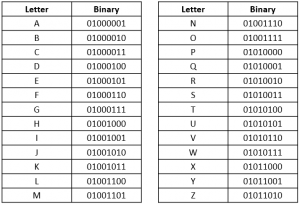
Gather pipe cleaners and two different colors of pony beads. One color will represent 0s and the other color will represent 1s. String the beads onto the pipe cleaner to represent your first initial. Twist the ends of the pipe cleaner together to make a bracelet. For example, my first initial is “R” and the equivalent byte is 01010010. My bracelet would look like this:

Don’t have pipe cleaners and beads at home? Feel free to use string, macaroni noodles, straw pieces, or whatever you have on hand that resembles beads! For a printable version of this activity, download this PDF.
Substitution Cipher
The last activity is a combination of the first two and can be done independently or as a final learning objective to sum up what’s been done in with the scytale and binary activities. In this activity each letter of the alphabet will be represented by something else. Each letter was represented by a byte, a combination of eight 0s and 1s. In a substitution cipher, a letter can be represented with anything – a number, a symbol, a picture, or even another letter.
Challenge your students to assign a new value to each letter of the alphabet. Then have them write an encrypted message for you or another student to decrypt. To decrypt the message, you’ll need a key! Refer to the student’s list of substitutions so that you can decrypt this message.
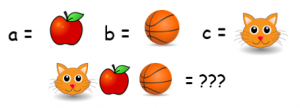
This activity brings in the concepts of encryption and decryption from scytale and the substitution nature of binary. Together, students can see how challenging it can be to encrypt and decrypt messages. Encryption is a huge part of computer science and it is the way we keep all our private information safe. In doing this activity, students can consider what makes for a secure method of encryption, how keys are involved, and what a hacker might do to intercept the decrypt the message without a key.
Looking for more unplugged activities for your classroom? Check out these reusable cipher wheels!






Leave A Comment